【Azure 应用服务】NodeJS Express + MSAL 实现API应用Token认证(AAD OAuth2 idToken)的认证实验 — passport.authenticate()
- 2022 年 6 月 11 日
- 笔记
- 【Azure Developer】, 【Azure 应用服务】, 【Azure 环境】, API Authorization Token, App Service, Azure Developer, Azure 环境, NodeJS + Express, passport.authenticate
问题描述
在前两篇博文中,对NodeJS Express应用 使用MSAL + AAD实现用户登录并获取用户信息,获取Authorization信息 ( ID Token, Access Token).
- 【Azure 应用服务】NodeJS Express + MSAL 应用实现AAD集成登录并部署在App Service Linux环境中的实现步骤
- 【Azure 应用服务】NodeJS Express + MSAL 应用实现AAD登录并获取AccessToken — cca.acquireTokenByCode(tokenRequest)
而在当前这篇博文中,我们将会实现以下目的:
1)为NodeJS API应用配置Bearer Token验证组件 passport 和 passport-azure-ad
2)实现使用idToken验证并访问API

实现步骤
在完成Azure AD中的注册应用配置并且根据博文“ NodeJS Express + MSAL 应用实现AAD登录并获取AccessToken — cca.acquireTokenByCode(tokenRequest): //www.cnblogs.com/lulight/p/16357246.html” 完成用户登录的前端应用后,参考官方示例 “Enable authentication in your own Node.js web API by using Azure Active Directory B2C : //docs.microsoft.com/en-us/azure/active-directory-b2c/enable-authentication-in-node-web-app-with-api”.
第一步:下载示例代码
git clone https://github.com/Azure-Samples/active-directory-b2c-javascript-nodejs-webapi.git
Install app dependencies
cd active-directory-b2c-javascript-nodejs-webapi
npm install
npm update
下载后的文件结构为:
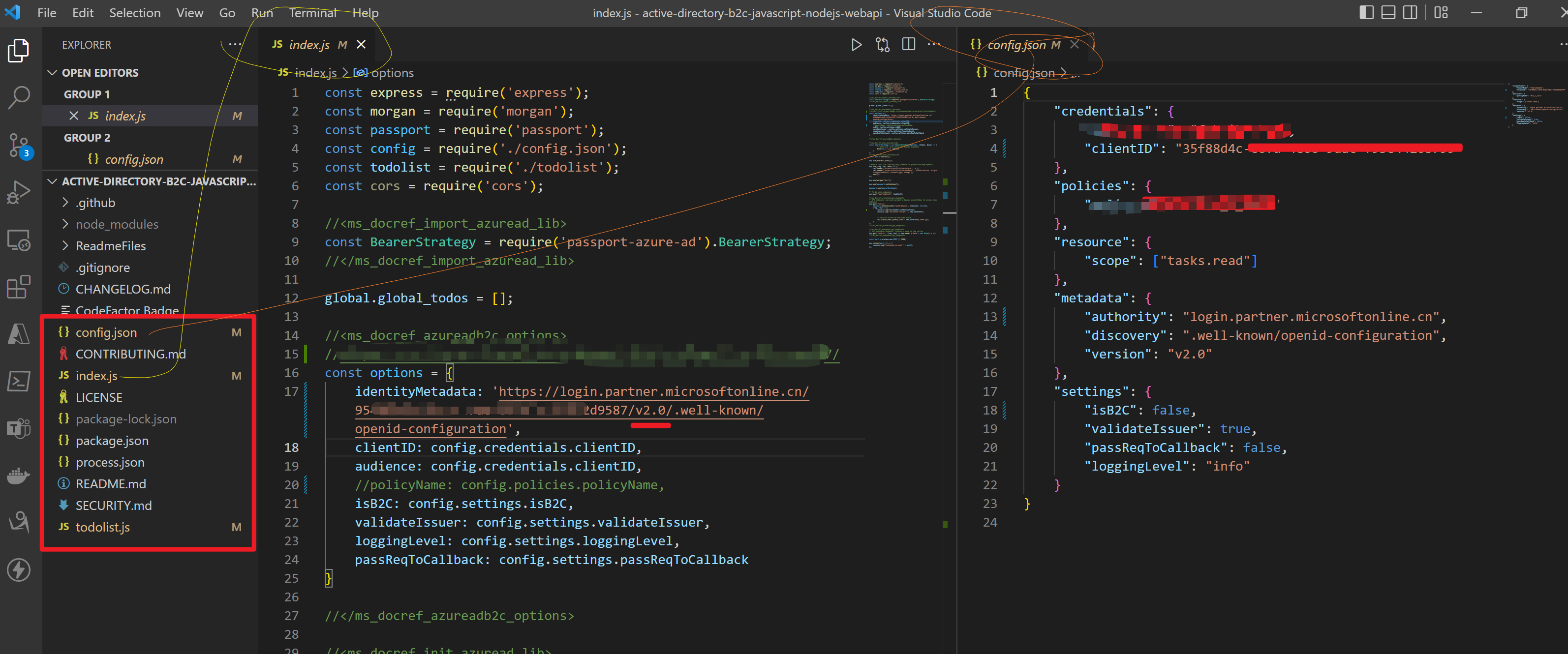
第二步:修改config.json 文件和index.js中的 identityMetadata 值
options中即为 BearerStrategy的配置参数,因为当前不适用AAD B2C,而是直接使用AAD,所以isB2C就需要设置为false,
const options = { identityMetadata: '//login.partner.microsoftonline.cn/xxxxxxxx-66d7-xxxx-8f9f-xxxxxxxxxxxx/v2.0/.well-known/openid-configuration', clientID: ##clientID, audience: ##clientID, validateIssuer: true, loggingLevel: 'info', passReqToCallback: false }
因为参考文档中使用的试AAD B2C来认证Token,而本示例中使用的是AAD来认证Token,所以很多参数配置有一点差别。 BearerStrategy的详细参数说明如下:
-
identityMetadata(Required)The metadata endpoint provided by the Microsoft Identity Portal that provides the keys and other important information at runtime. Examples:
- v1 tenant-specific endpoint
//login.microsoftonline.com/your_tenant_name.onmicrosoft.com/.well-known/openid-configuration //login.microsoftonline.com/your_tenant_guid/.well-known/openid-configuration- v1 common endpoint
//login.microsoftonline.com/common/.well-known/openid-configuration- v2 tenant-specific endpoint
//login.microsoftonline.com/your_tenant_name.onmicrosoft.com/v2.0/.well-known/openid-configuration //login.microsoftonline.com/your_tenant_guid/v2.0/.well-known/openid-configuration- v2 common endpoint
//login.microsoftonline.com/common/v2.0/.well-known/openid-configurationFor B2C, you can only use v2 tenant-specific endpoint.
-
clientID(Required)The client ID of your application in AAD (Azure Active Directory)
-
passReqToCallback(Conditional)Required to set to true if using
reqas the first paramter in the verify function, default value is false. See section 4.2.1.3 for more details. -
isB2C(Conditional)Required to set to true if you are using B2C tenant.
-
policyName(Conditional)Required if you are using B2C tenant. It is a string starting with ‘B2C_1_’ (case insensitive).
-
validateIssuer(Conditional)Required to set to false if you don’t want to validate issuer, default value is true. We validate the
issclaim in id_token against user providedissuervalues and the issuer value we get from tenant-specific endpoint. If you use common endpoint foridentityMetadataand you want to validate issuer, then you must provideissuer, or providetenantIdOrNamein passport.authenticate. -
issuer(Conditional)This can be a string or an array of strings. See
validateIssuerfor the situation that requiresissuer. -
allowMultiAudiencesInToken(Conditional)Required if you allow access_token whose
audclaim contains multiple values. -
scope(Optional)This value is an array of scopes you accept. If this value is provided, we will check if the token contains one of these accepted scopes. If this value is not provided, we won’t check token scopes.
-
audience(Optional)Must be a string or an array of strings. We invalidate the
audclaim in access_token againstaudience. The default value foraudienceisclientID. -
loggingLevel(Optional)Logging level. ‘info’, ‘warn’ or ‘error’.
-
loggingNoPII(Optional)If this is set to true, no personal information such as tokens and claims will be logged. The default value is true.
-
clockSkew(Optional)This value is the clock skew (in seconds) allowed in token validation. It must be a positive integer. The default value is 300 seconds.
-
proxy(optional)
This value is the proxy settings object: { port: ‘proxyport’, host: ‘proxyhost’, protocol: ‘http’ }
文档地址://github.com/AzureAD/passport-azure-ad#42-bearerstrategy
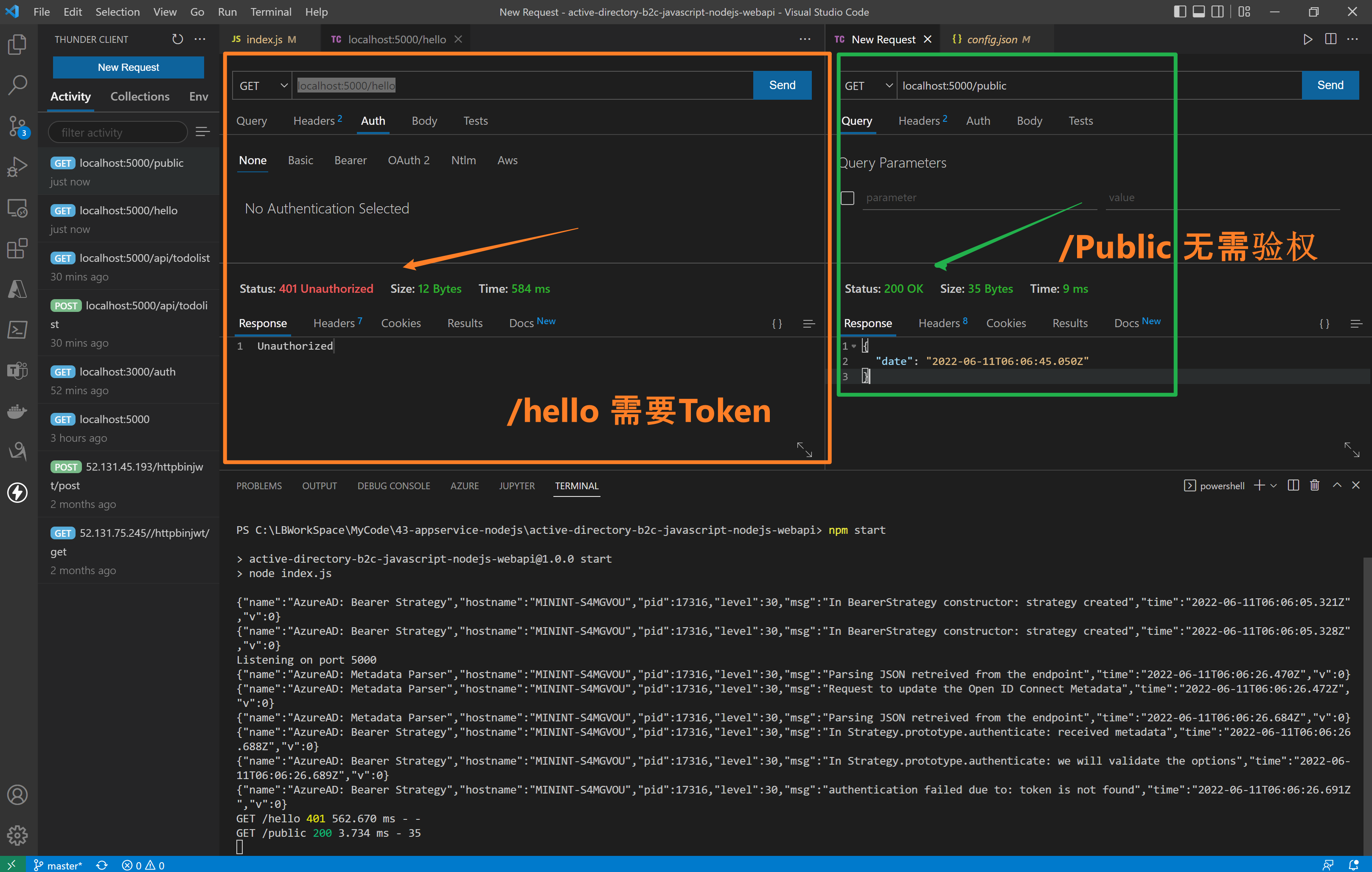
第三步:访问API接口(/hello 需要Authorization, /public 不需要Authorization)
在index.js代码中,实现了两个接口 /hello 和 /public。 /hello 接口添加了passport.authenticate认证,访问需要携带Authorization (JWT Token),而/public则无需认证。
//<ms_docref_protected_api_endpoint> // API endpoint, one must present a bearer accessToken to access this endpoint app.get('/hello', passport.authenticate('oauth-bearer', {session: false}), (req, res) => { console.log(req.headers.authorization); console.log('Validated claims: ', req.authInfo); // Service relies on the name claim. res.status(200).json({'name': req.authInfo['name']}); } ); //</ms_docref_protected_api_endpoint> //<ms_docref_anonymous_api_endpoint> // API anonymous endpoint, returns a date to the caller. app.get('/public', (req, res) => res.send( {'date': new Date() } )); //</ms_docref_anonymous_api_endpoint>
验证效果:
第四步:验证 idToken 和 accessToken
在前端UI页面通过登录后获取到Token信息, //localhost:3000/auth

验证展示动画:
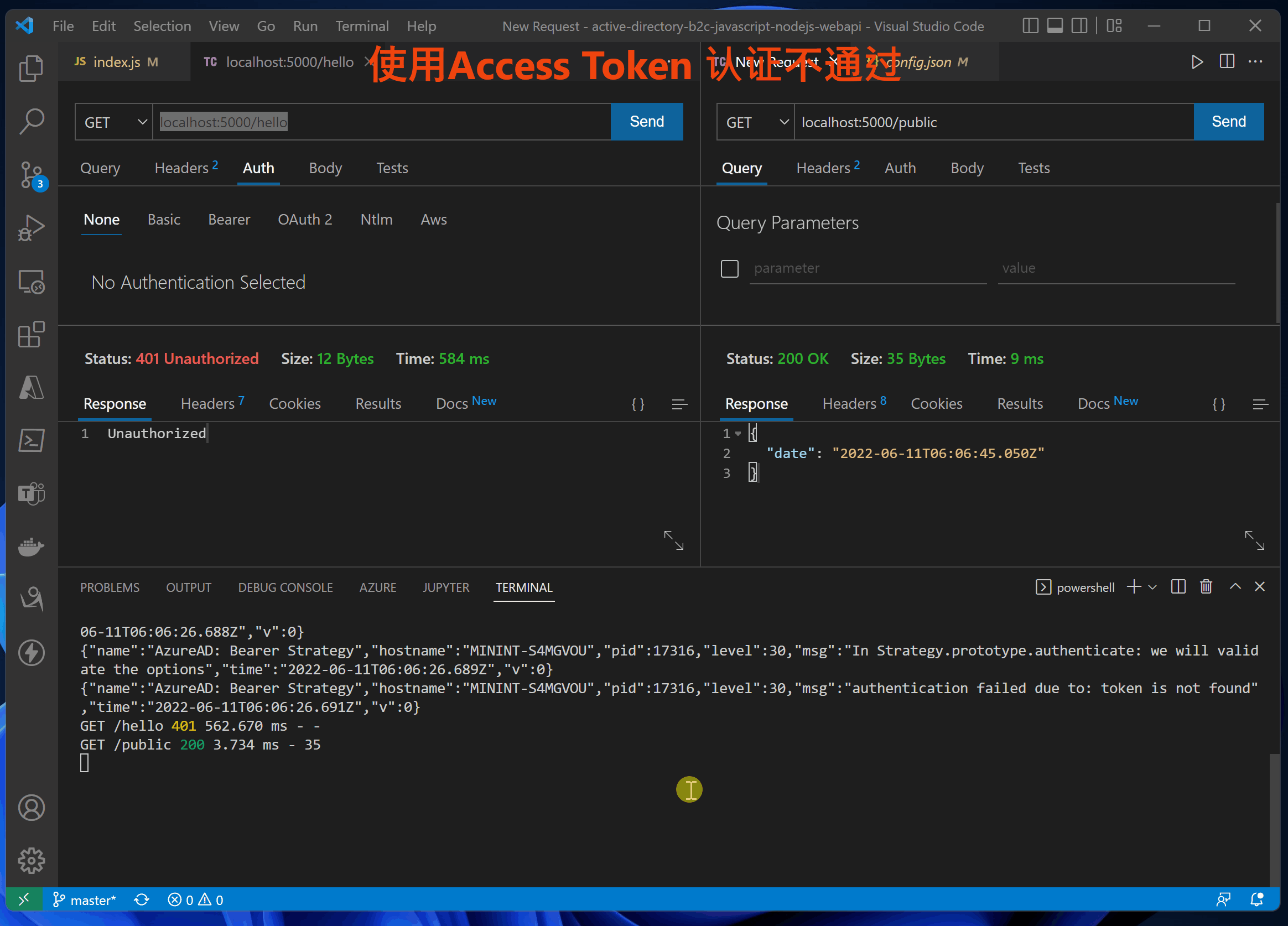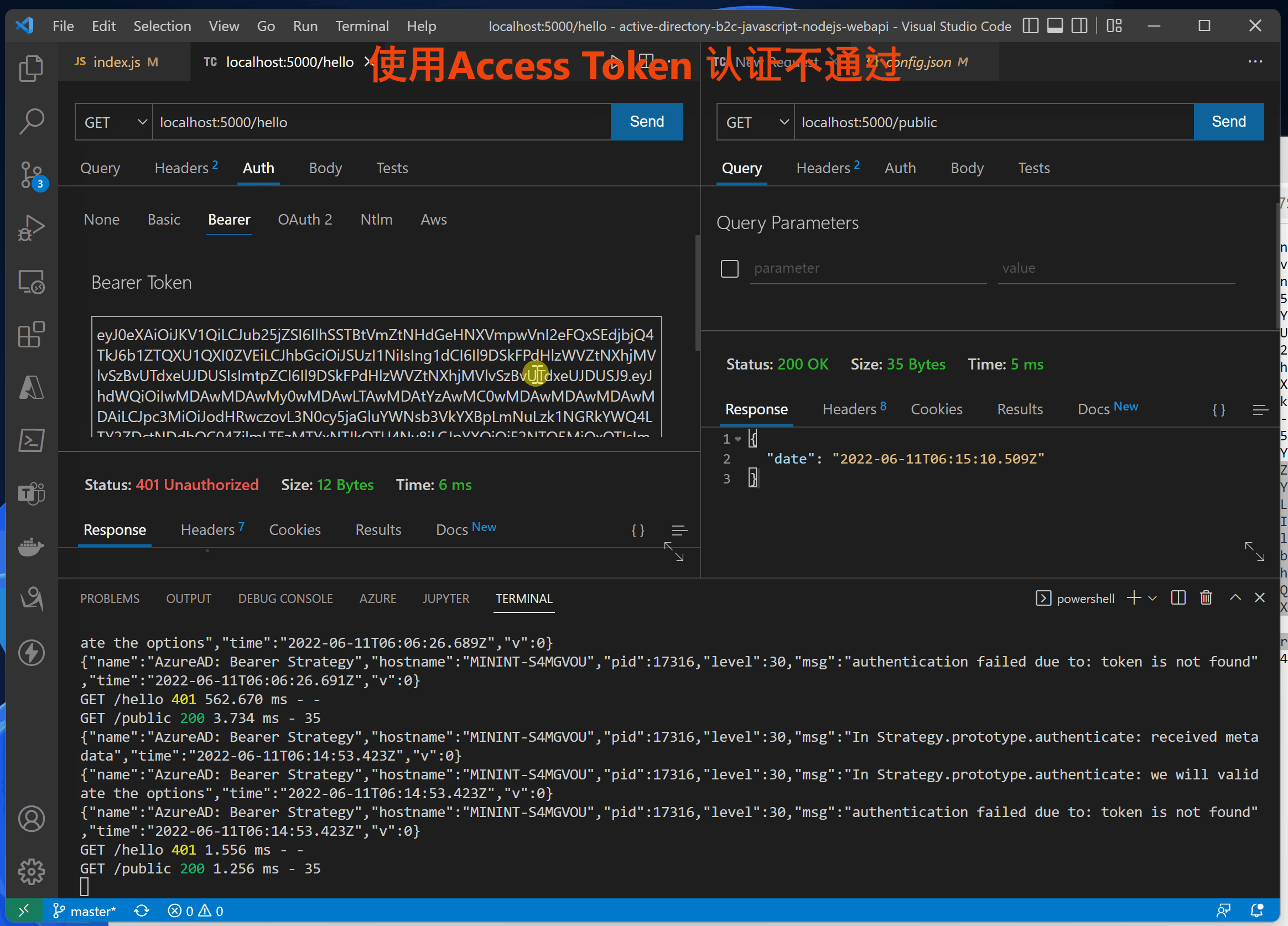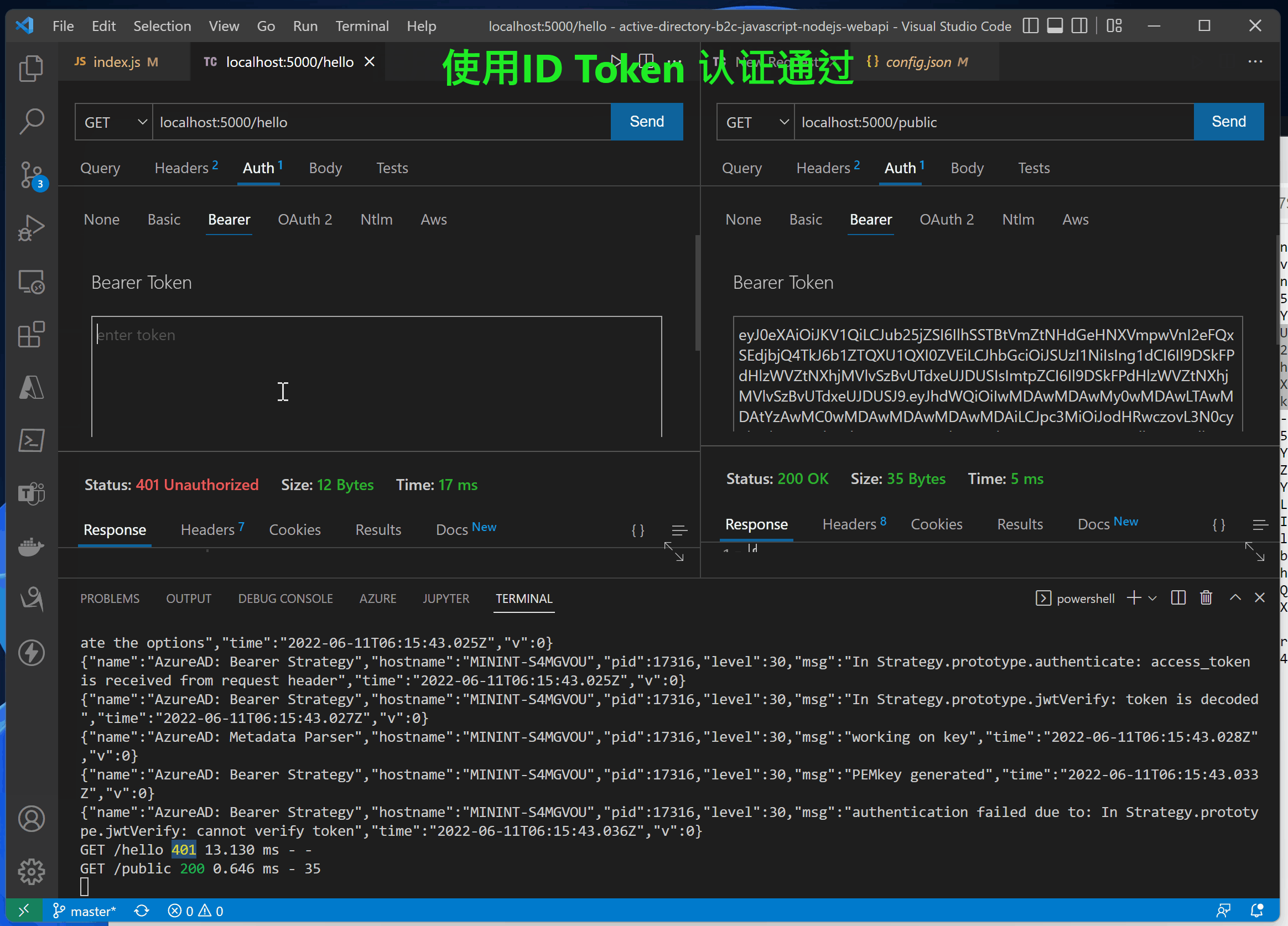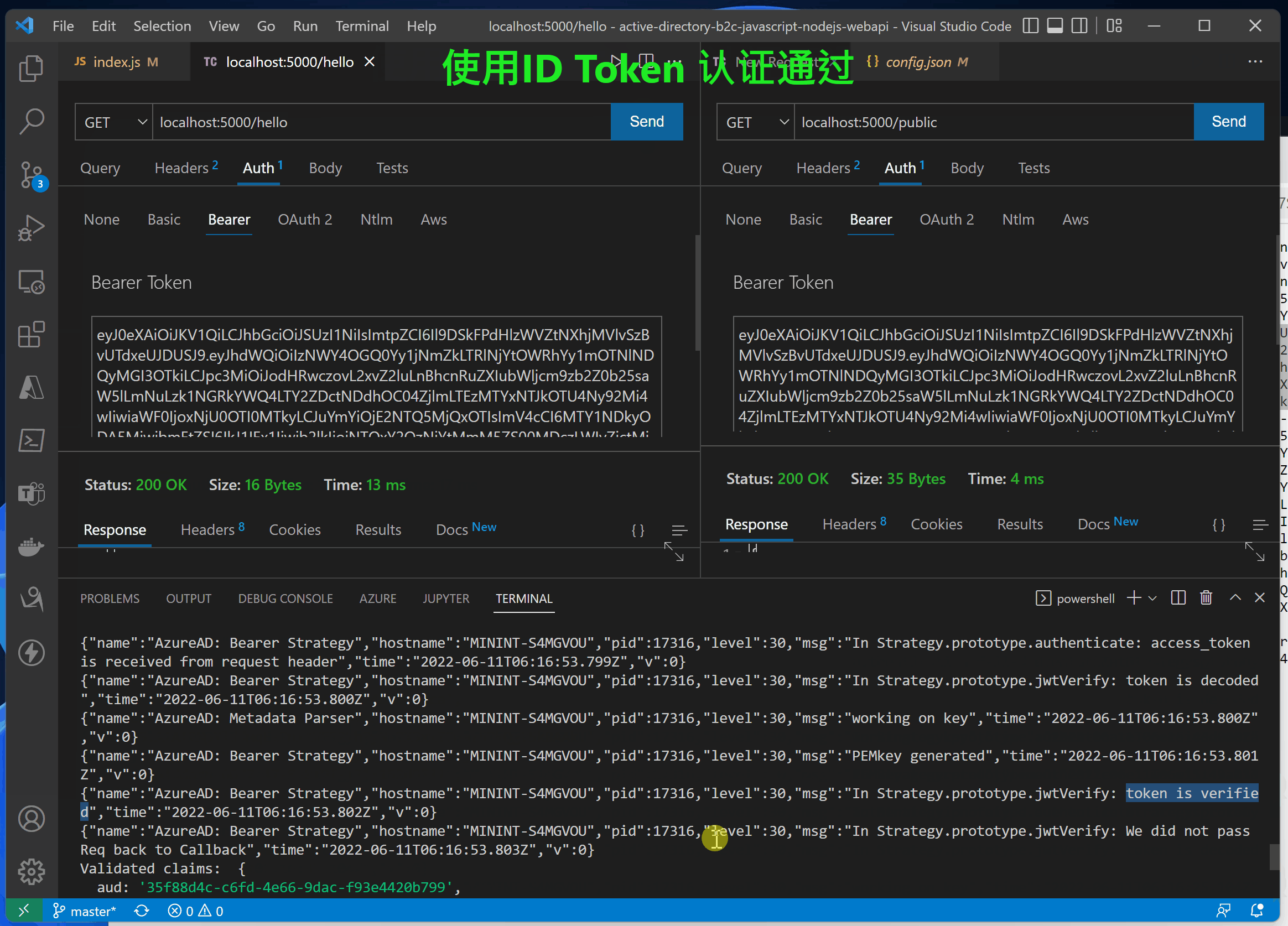
使用accessTokne的错误日志
{“name”:”AzureAD: Bearer Strategy”,”hostname”:”MININT-S4MGVOU”,”pid”:17316,”level”:30,”msg”:”In Strategy.prototype.authenticate: received metadata”,”time”:”2022-06-11T06:15:43.024Z”,”v”:0}
{“name”:”AzureAD: Bearer Strategy”,”hostname”:”MININT-S4MGVOU”,”pid”:17316,”level”:30,”msg”:”In Strategy.prototype.authenticate: we will validate the options”,”time”:”2022-06-11T06:15:43.025Z”,”v”:0}
{“name”:”AzureAD: Bearer Strategy”,”hostname”:”MININT-S4MGVOU”,”pid”:17316,”level”:30,”msg”:”In Strategy.prototype.authenticate: access_token is received from request header”,”time”:”2022-06-11T06:15:43.025Z”,”v”:0}
{“name”:”AzureAD: Bearer Strategy”,”hostname”:”MININT-S4MGVOU”,”pid”:17316,”level”:30,”msg”:”In Strategy.prototype.jwtVerify: token is decoded”,”time”:”2022-06-11T06:15:43.027Z”,”v”:0}
{“name”:”AzureAD: Metadata Parser”,”hostname”:”MININT-S4MGVOU”,”pid”:17316,”level”:30,”msg”:”working on key”,”time”:”2022-06-11T06:15:43.028Z”,”v”:0}
{“name”:”AzureAD: Bearer Strategy”,”hostname”:”MININT-S4MGVOU”,”pid”:17316,”level”:30,”msg”:”PEMkey generated”,”time”:”2022-06-11T06:15:43.033Z”,”v”:0}
{“name”:”AzureAD: Bearer Strategy”,”hostname”:”MININT-S4MGVOU”,”pid”:17316,”level”:30,”msg”:”authentication failed due to: In Strategy.prototype.jwtVerify: cannot verify token“,”time”:”2022-06-11T06:15:43.036Z”,”v”:0}
GET /hello 401 1.556 ms – –
使用idToken的正确日志
{"name":"AzureAD: Bearer Strategy","hostname":"MININT-S4MGVOU","pid":17316,"level":30,"msg":"In Strategy.prototype.authenticate: received metadata","time":"2022-06-11T06:16:25.102Z","v":0}
{"name":"AzureAD: Bearer Strategy","hostname":"MININT-S4MGVOU","pid":17316,"level":30,"msg":"In Strategy.prototype.authenticate: we will validate the options","time":"2022-06-11T06:16:25.102Z","v":0}
{"name":"AzureAD: Bearer Strategy","hostname":"MININT-S4MGVOU","pid":17316,"level":30,"msg":"In Strategy.prototype.authenticate: access_token is received from request header","time":"2022-06-11T06:16:25.103Z","v":0}
{"name":"AzureAD: Bearer Strategy","hostname":"MININT-S4MGVOU","pid":17316,"level":30,"msg":"In Strategy.prototype.jwtVerify: token is decoded","time":"2022-06-11T06:16:25.104Z","v":0}
{"name":"AzureAD: Metadata Parser","hostname":"MININT-S4MGVOU","pid":17316,"level":30,"msg":"working on key","time":"2022-06-11T06:16:25.104Z","v":0}
{"name":"AzureAD: Bearer Strategy","hostname":"MININT-S4MGVOU","pid":17316,"level":30,"msg":"PEMkey generated","time":"2022-06-11T06:16:25.105Z","v":0}
{"name":"AzureAD: Bearer Strategy","hostname":"MININT-S4MGVOU","pid":17316,"level":30,"msg":"In Strategy.prototype.jwtVerify: token is verified","time":"2022-06-11T06:16:25.107Z","v":0}
{"name":"AzureAD: Bearer Strategy","hostname":"MININT-S4MGVOU","pid":17316,"level":30,"msg":"In Strategy.prototype.jwtVerify: We did not pass Req back to Callback","time":"2022-06-11T06:16:25.107Z","v":0}
Validated claims: {
aud: 'xxxxx-c6fd-xxx-9dac-xxxxxx',
iss: '//login.partner.microsoftonline.cn/xxxxx-c6fd-xxx-9dac-xxxxxx/v2.0',
iat: 1654924192,
nbf: 1654924192,
exp: 1654928092,
name: 'your name here',
oid: 'xxxxx-c6fd-xxx-9dac-xxxxxx',
preferred_username: '[email protected]',
rh: '0.xxxxxxxxx-xxxxxxxxxxxxxx.',
sub: 'xxxxxxxxxxxxxxxxxxxxxxxxxxxx',
tid: 'x-66d7-47a8-xx-xxx',
uti: 'xxxxxxxxxxxxxxxxxxxxxxxxx',
ver: '2.0'
}
GET /hello 200 11.557 ms - 16
[可选]第五步:修改AAD注册应用的accessTokenAcceptedVersion
因为中国区AAD目前生成的Token为OAuth v1.0, 而在API应用中 identityMetadata 使用的是v2.0的openid-configration。所以需要在ADD中修改当前注册应用的清单文件(Mainfest)中
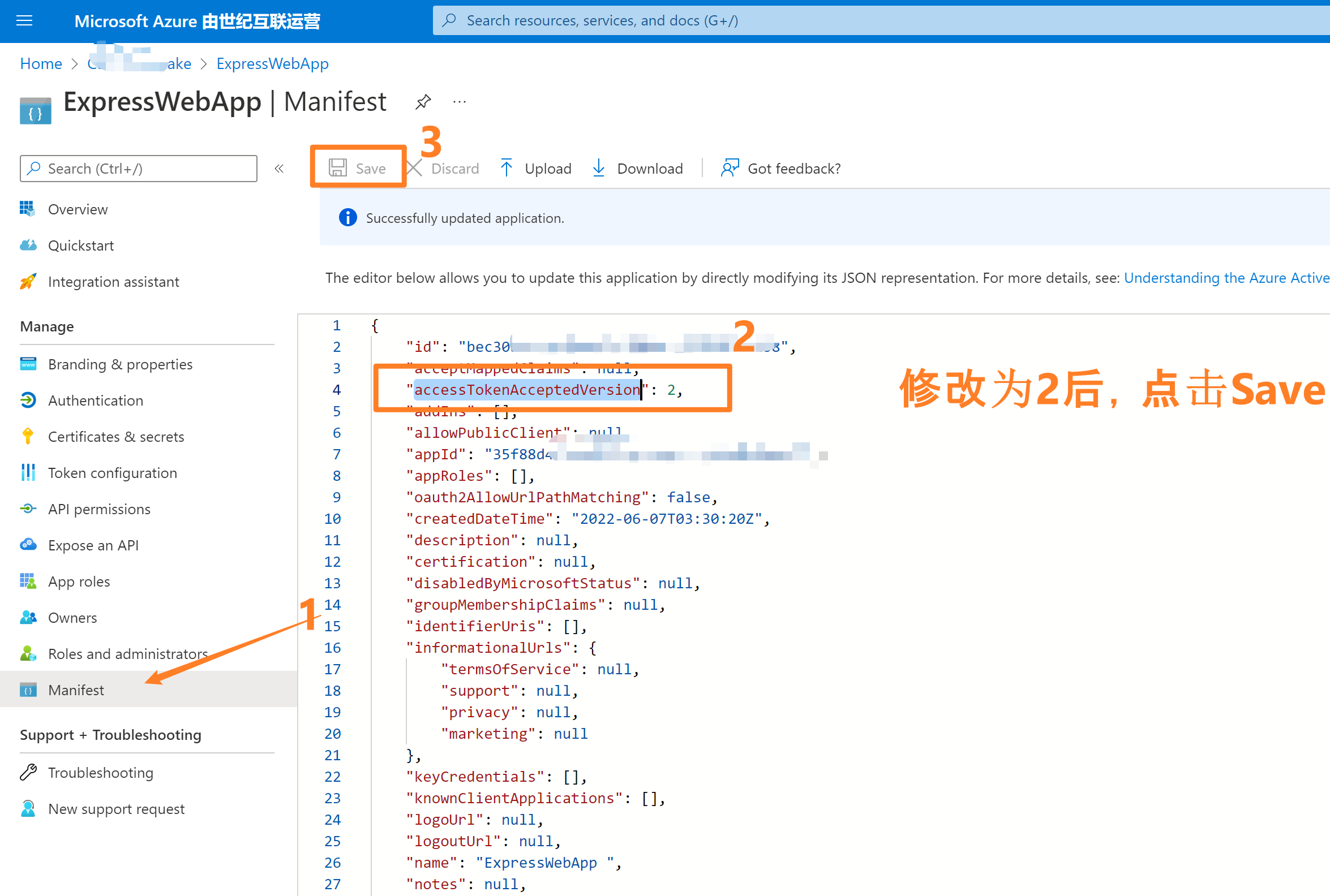
- 登录Azure 门户,选择Azure AD。
- 点击 App registrations 并选择自己的应用,如本示例中的“ExpressWebApp”
- 进入应用Overview页面后,选择左侧导航中“Manifest”清单页面。修改 accessTokenAcceptedVersion 的值为2,保存即可。
参考资料
Configure authentication in a sample Node.js web API by using Azure Active Directory B2C: //docs.microsoft.com/en-us/azure/active-directory-b2c/configure-authentication-in-sample-node-web-app-with-api#step-4-get-the-web-api-sample-code
Microsoft Azure Active Directory Passport.js Plug-In://github.com/AzureAD/passport-azure-ad#42-bearerstrategy
Tutorial: Sign in users and acquire a token for Microsoft Graph in a Node.js & Express web app: //docs.microsoft.com/en-us/azure/active-directory/develop/tutorial-v2-nodejs-webapp-msal
Example: Acquiring tokens with ADAL Node vs. MSAL Node://docs.microsoft.com/en-us/azure/active-directory/develop/msal-node-migration#example-acquiring-tokens-with-adal-node-vs-msal-node
NodeJS Express + MSAL 应用实现AAD集成登录并部署在App Service Linux环境中的实现步骤://www.cnblogs.com/lulight/p/16353145.html
NodeJS Express + MSAL 应用实现AAD登录并获取AccessToken — cca.acquireTokenByCode(tokenRequest)://www.cnblogs.com/lulight/p/16357246.html


