CTF-BugKu-34-很普通的数独-独家脚本解法
2020.09.15
做得好慢,,,心不在焉的,赶紧的啊,还得做别的呢
做题
第三十四题 很普通的数独(ISCCCTF)
//ctf.bugku.com/challenges#很普通的数独(ISCCCTF)

- zip没有后缀,winhex打开,发现确实是zip,修改后缀,解压得到一堆图片,内容是数独
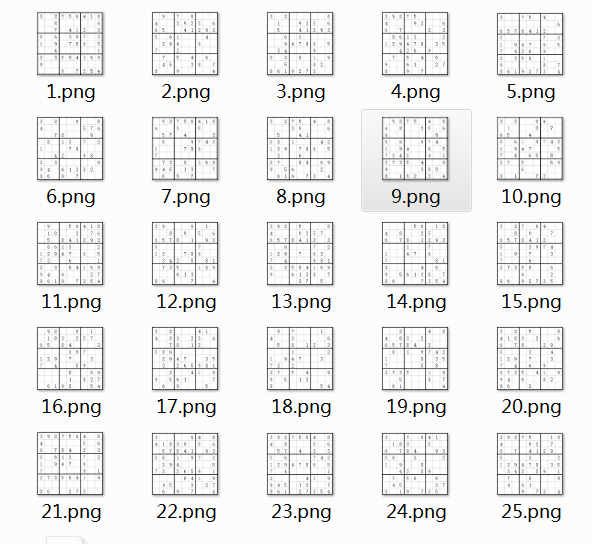
- 非常壮观,出题人也是费劲了,这个就是二维码分成了25部分,把有数字的涂黑,拼到一起就能组成一个二维码,思路是看来的,但是怎么才能快速完成这一系列的工作呢,怎么能快速获取黑点呢,全点一遍有点呆吧……
- 每一个有九行,如果能选某一行的像素点遍历,估计就可以实现了,go,
(n years later……)
他终于来了,全网独家脚本,哈哈哈哈哈哈,可能没人和我这么闲吧哈哈哈哈
此时文件结构是这样的:
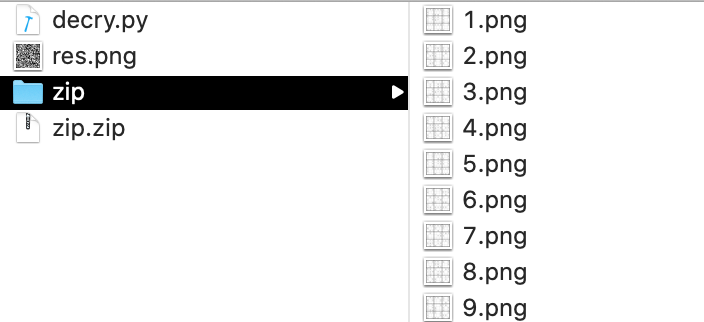
# 此脚本用于从数独图片获取密码,有值为1,无值为0
import os
import cv2
import numpy as np
from PIL import Image
black = (0,0,0)
white = (255,255,255)
def getBin(picPath):
image = cv2.imread(picPath)
height = image.shape[0] # 图片宽度
wide = image.shape[1] # 图片高度
formWide = (wide-6)/9 # 每一格宽度
res = []
tem = ''
for i in range(9):
for j in range(wide-6):
px = image[int(i*(formWide-1)+(formWide/2)), j+3]
if (px == white).all() and (j+3)%formWide > (formWide*3/4) and (j+3)/formWide > len(tem):
tem += '0'
if (px == black).all() and (j+3) % formWide > (formWide/4) and (j+3) % formWide < (3*formWide/4) and (j+3)/formWide > len(tem):
tem += '1'
res.append(tem)
tem = ''
return res
def getRes():
tem = [] # 临时存储返回值
res = [] # 存储结果数组
for i in range(5):
for j in range(5):
picPath = 'zip/' + str(i*5+j+1) + '.png' # 构造文件名
tem = getBin(picPath)
if len(res)==0:
res = tem
else:
if len(res)==(i+1)*9:
for x in range(len(tem)):
res[(i*9)+x] += tem[x]
else:
for x in range(len(tem)):
res.append(tem[x])
return res
resList = getRes()
resImg = Image.new('RGB',(45,45))
for x in range(45):
for y in range(45):
if resList[x][y] == '0':
resImg.putpixel((x,y),white)
else:
resImg.putpixel((x,y),black)
resImg.save('res.png')
-
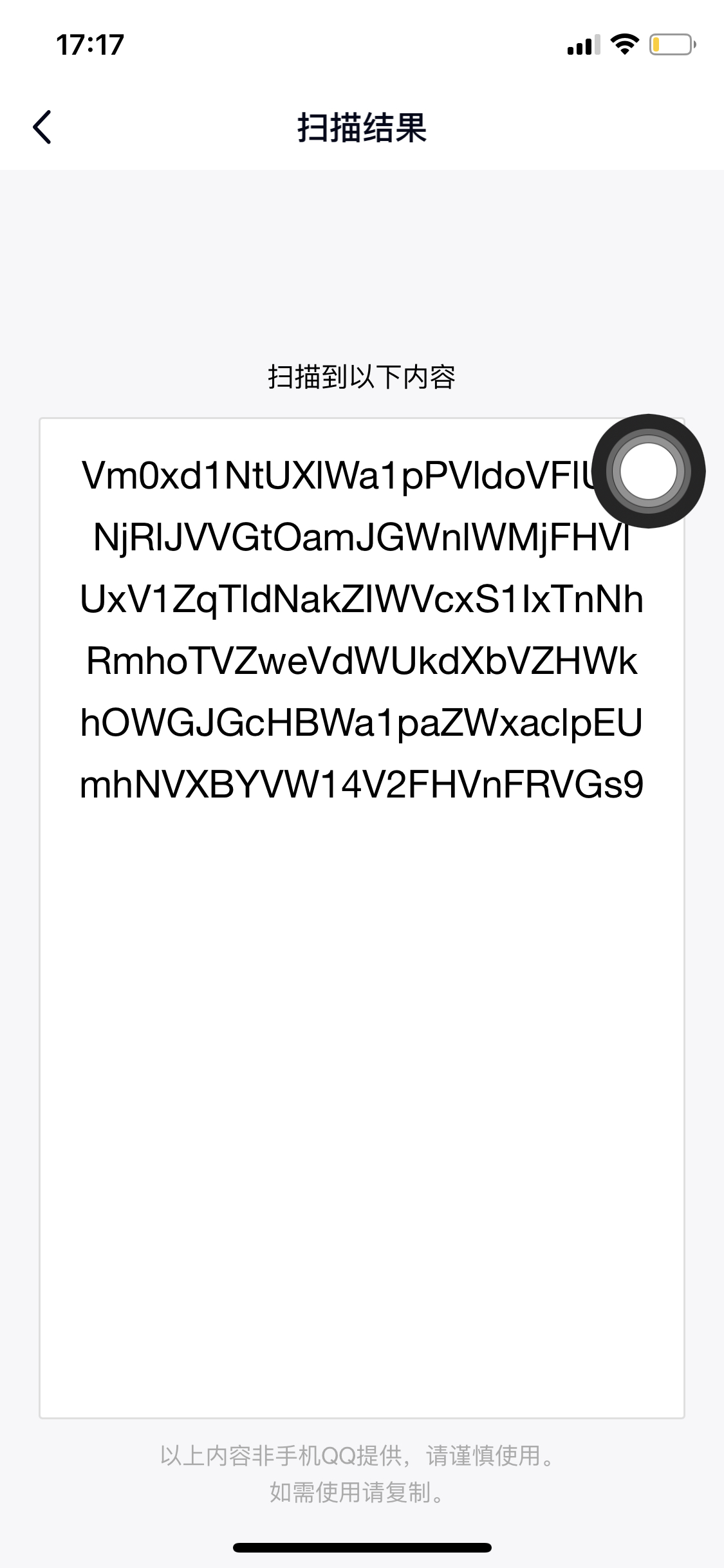
脚本获取的图片还是有一些偏差,因为题目给的图片不规范(不管我的事
),我微调脚本之后,得到下图,QR Search竟然扫不出来,但是腾讯QQ可以,我只能说一句马老板
哈哈哈哈哈,扫码结果:
Vm0xd1NtUXlWa1pPVldoVFlUSlNjRlJVVGtOamJGWnlWMjFHVlUxV1ZqTldNakZIWVcxS1IxTnNhRmhoTVZweVdWUkdXbVZHWkhOWGJGcHBWa1paZWxaclpEUmhNVXBYVW14V2FHVnFRVGs9

-
base64解码七次后结果:
flag{y0ud1any1s1}







